-
Rising Threats: How AI Amplifies Cybersecurity Risks
ImageSrc: Enisa AI has been around for a while but the recent surge and adoption of generative AI solutions such as ChatGPT, BARD and others are now a hotbed for cybersecurity actors and threats. In this post lets explore some of the security challenges we can expect in the age of Generative AI and AI…
-
Deep dive into the PXE Boot Process
PXE (Preboot Execution Environment) booting has been a game-changer for me when it comes to managing and deploying operating systems across multiple machines. Instead of manually installing an OS on each system using a USB drive or disk, PXE allows me to boot and load the OS directly from the network, making the whole process…
-
Unified Update Platform (UUP) and Why You Should Care
If you’re managing Windows devices in any capacity, whether you’re an IT administrator or just someone responsible for keeping systems running smoothly, the introduction of Microsoft’s Unified Update Platform (UUP) is something you should absolutely be aware of. The way we handle updates is evolving, and UUP is at the forefront of this change. Let…
-
Keeping Browser Extensions in Check
In the last week there has been a tremendous malware campaign exploiting Browser extensions. Read more about it here –https://www.csa.gov.sg/alerts-advisories/alerts/2024/al-2024-107 Why Browsers? Think about it – the browser is the single most random code execution environment on the endpoint. You go to a website and to render that website the browser downloads and runs client…
-
Autonomous Endpoint Management – Part 2
Following up on the first post on this topic, this post explores what are the key capabilities that AEM will deliver in the years ahead. There are a few key business outcomes that AEM will deliver on Given the common challenges faced for Endpoint Management, these are the top 5 biggest outcomes AEM will deliver…
-
Impact of the Australian Government PSPF Direction 002-2024

Amidst all the complexities of managing IT environments, increased regulation more than anything else is single handedly responsible for cost overruns and an increased war on talent. On the positive side, this has meant better protected environments, accountability and retirement of legacy technologies and architectures. The PSPF (Protective Security Policy Framework) Directive 002-2024 which is…
-
Malaysia Cyber Act 854

Overview of the Act The Cyber Security Act 2024 has been officially gazetted by the Attorney General’s Chambers on 26 June 2024. This legislation is a major milestone in strengthening Malaysia’s cyber defenses and enhancing cyber resilience against a constantly evolving threat landscape. The Act introduces requirements designed to improve and monitor the security of…
-
The World grinds to a HALT!! Again!!
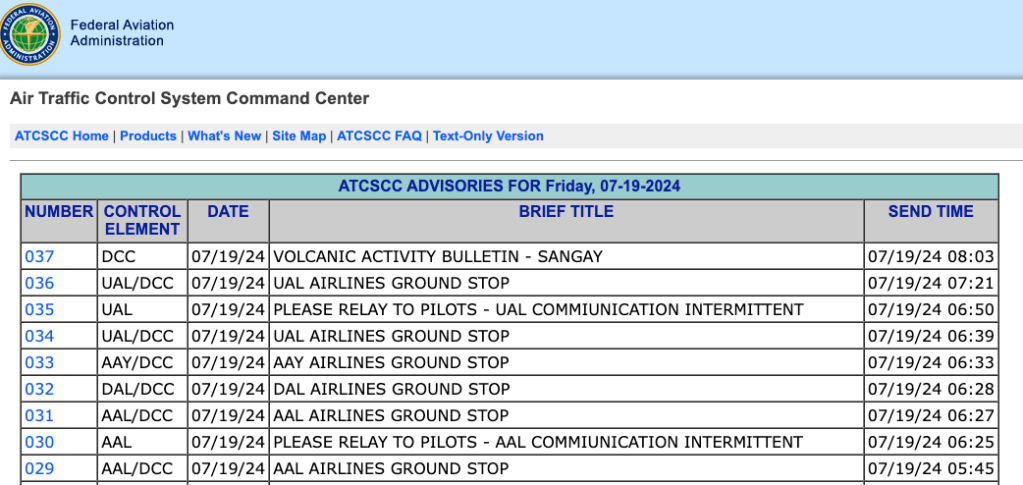
I remember being at a Barbecue on a Saturday evening in July 2017 and I got asked by a friend who doesn’t work in Information Technology – what is ransomware? It was around the first time that I can remember that cyberattacks became common knowledge. Everyday users would have heard about cyber risks but this…
-
Autonomous Endpoint Management – Part 1
A recent Hype Cycle for IT Management Intelligence publication by Gartner stood out for the vision of the future of Endpoint Management. With the increasing adoption of AI, there is an increased focus by vendors to use the data gathered from endpoint to focus on not just automating but also delivering safe autonomous outcomes for…
-
NIST SP 800-207: Zero Trust Architecture
I was recently invited to speak at a Zero Trust Strategies conference in the Philippines by one of the local Systems Integrators. I must admit that during this time is the first time I read the NIST Special Publication 800-207 on Zero Trust Architecture (ZTA) and it had some fascinating insights. Lets look at NIST definition…
Security Bytes
Cybersecurity learnings in byte sized posts
