I was recently invited to speak at a Zero Trust Strategies conference in the Philippines by one of the local Systems Integrators. I must admit that during this time is the first time I read the NIST Special Publication 800-207 on Zero Trust Architecture (ZTA) and it had some fascinating insights. Lets look at NIST definition of Zero Trust
Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. A zero trust architecture (ZTA) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned). Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established. Zero trust is a response to enterprise network trends that include remote users, bring your own device (BYOD), and cloud-based assets that are not located within an enterprise- owned network boundary. Zero trust focuses on protecting resources (assets, services, workflows, network accounts, etc.), not network segments, as the network location is no longer seen as the prime component to the security posture of the resource. This document contains an abstract definition of zero trust architecture (ZTA) and gives general deployment models and use cases where zero trust could improve an enterprise’s overall information technology security posture.
Over the years, the network infrastructure for traditional enterprises has grown increasingly complex, and perimeter-based network security controls are not effective in dealing with modern threats. This has led to the development of the zero trust (ZT) security model, which moves away from the implicit trust lent by a network location and towards a continual validation of the identity and security posture of each access request. ZT is not a single architecture or product but a set of guiding principles to improve the security posture of an organization, and the transition to a ZTA will require technology and process changes over time.
Tenets of Zero Trust
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy – including the observable state of client identity, application/service, and the requesting asset – and may include other behavioural and environmental attributes.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications and uses it to improve its security posture.
A Zero Trust View of a Network (Assumptions)
- The entire enterprise private network is not considered as implicit trust zone.
- Devices on the network may not be owned or configurable by the enterprise.
- No resource is inherently trusted.
- Not all enterprise resources are on enterprise-owned infrastructure.
- Remote enterprise subjects and assets cannot fully trust their local network connection.
- Assets and workflows moving between enterprise and non-enterprise infrastructure should have a consistent security policy and posture.
Logical Components of Zero Trust Architecture
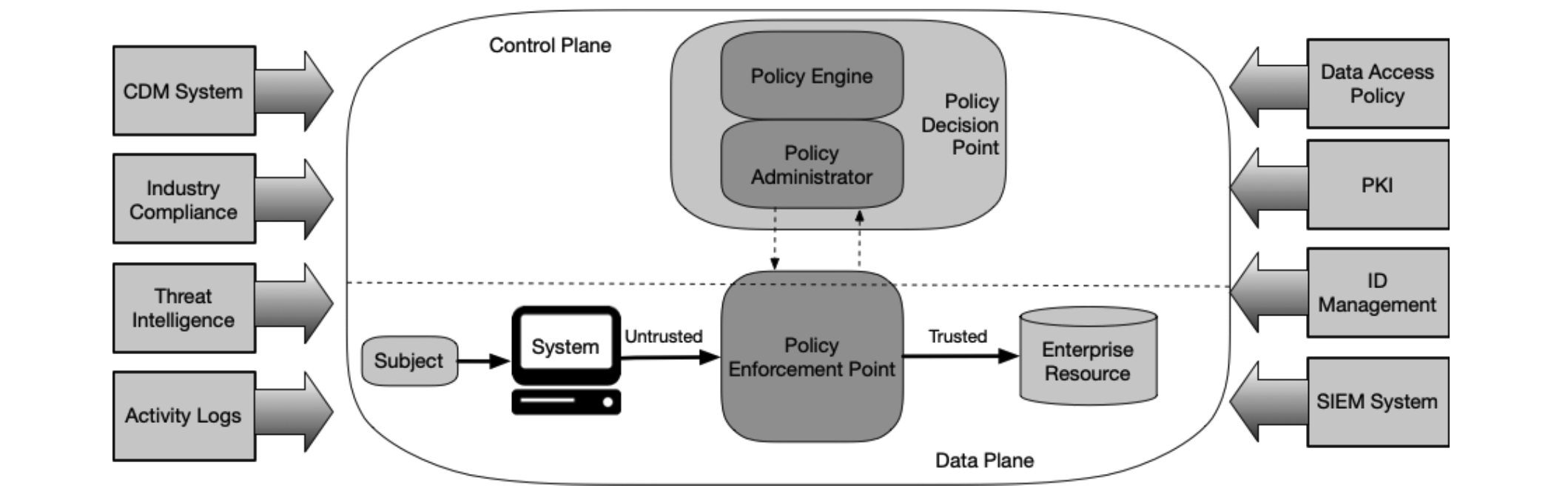
ZTA Approaches
- ZTA using enhanced identity governance: uses the identity and attributes of actors as the key component of policy creation; may be augmented by device status, asset status and environmental factors.
- ZTA using micro-segmentation: places resources on unique network segments protected by gateway security components; may implement host-based micro-segmentation using agents too.
- ZTA using network infrastructure and software defined perimeters: uses an overlay network i.e. software-defined perimeter approach.
ZTA Deployment Models
- Device agent/gateway-based deployment: an agent on enterprise-issued assets to coordinate connections, and a gateway/proxy in front of the protected resources to approve connection requests; does not support BYOD.
- Enclave-based deployment: variation of the above model with all resources within an enclave protected by the same gateway/proxy; does not protect each resource individually, increasing the blast radius of a compromise.
- Resource portal-based deployment: no agent on enterprise assets, resulting in limited visibility into device health; supports BYOD.
- Device application sandboxing: enterprise assets run approved, vetted applications inside a sandbox; leads to increase in maintenance overheads.

Leave a comment